As a lot of us have already seen (in this post https://www.reddit.com/r/linux4noobs/comments/1op33pa/ransomware_help/). Linux adoption is on the rise. We used to be told not to care for viruses because hackers just don't care but here we are. So what are you guys using as antivirus measures?
[link] [comments]
/// 5 Nov 2025, 5:48 pm ////// GamingOnLinux ///
 .
.
Read the full article on GamingOnLinux.
/// 5 Nov 2025, 6:44 pm ////// Tux Machines ///
/// 6 Nov 2025, 1:37 am ////// Phoronix ///
SUSE becomes the first open source company to adopt agentic AI with SUSE Enterprise Linux 16.
Xray_OS is an Arch-based distribution which bills itself as cutting-edge but with a touch of innovation
The post Xray_OS – Arch-based Linux distribution appeared first on LinuxLinks.
/// 4 Nov 2025, 3:36 pm ////// LINUXTODAY ///
Major Uptime Kuma 2.0 update adds MariaDB, rootless Docker, and a refreshed UI for smoother, faster self-hosted monitoring.
The post Uptime Kuma 2.0 Arrives with MariaDB Support, Modern UI Refresh appeared first on Linux Today.
/// 4 Nov 2025, 6:40 pm ////// FSF Blog ///
/// 5 Nov 2025, 11:20 am ////// ITS FOSS ///

With recent developments, such as the introduction of a reference operating system, the GNOME project has clearly positioned itself as a full, top-to-bottom computing platform. It has one of the fastest-growing app ecosystems in the Linux and open-source world as a whole and even has an Incubator, providing a path for some apps to join Core via the Release Team. GNOME-adjacent, community-led projects like Phosh build on this robust ecosystem to deliver their unified vision to other form factors.
Yet, one of the jarringly obvious things the GNOME platform lacks right now is a dedicated office suite that follows its Human Interface Guidelines (HIG) and uses its native technologies. This brings us to the question: Is it time for a resurrection?
GNOME Office of the past
For those who aren't familiar, it's probably best if we take a step back in history and look at what exactly GNOME Office was — and, technically, still "is" in a loose sense.
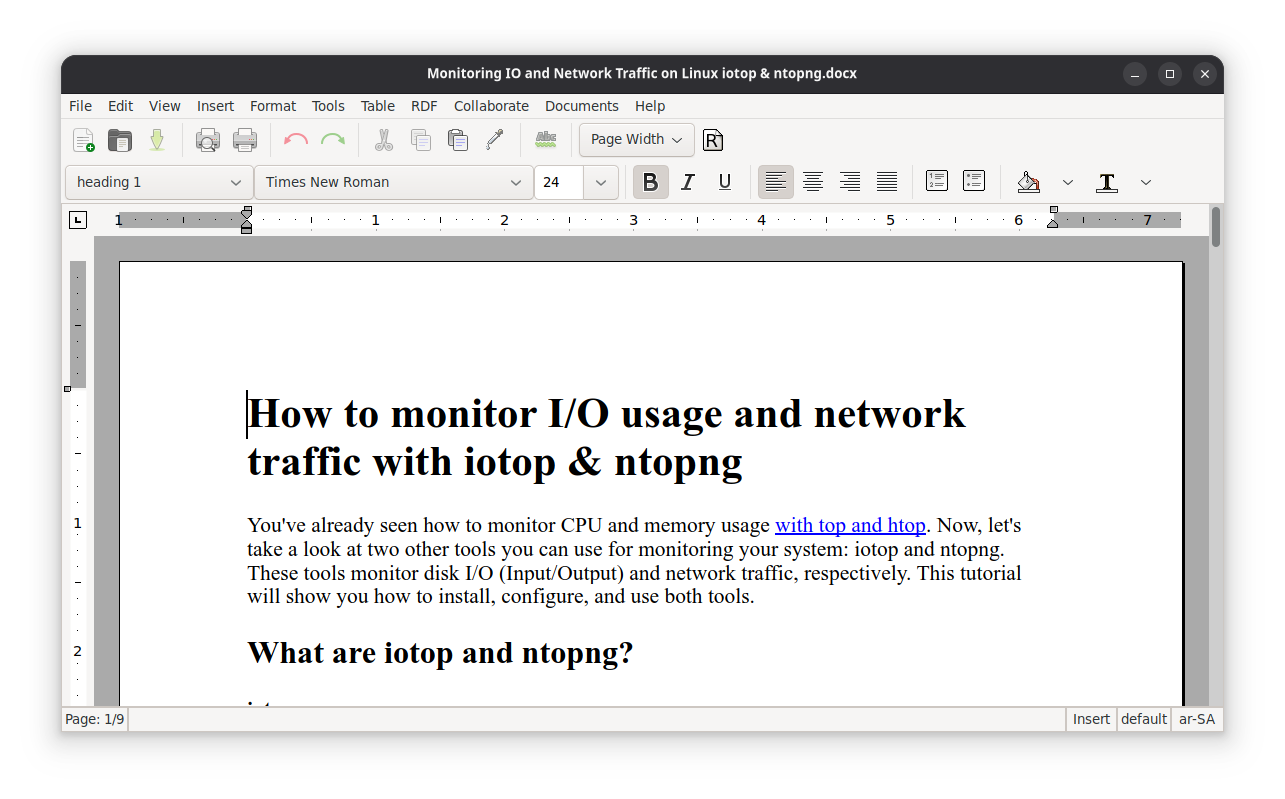
Back in the days of GNOME 2, circa the early 2000s, there was a loose effort to establish an open-source, GTK-based office suite from the sum of existing parts. The 1.0 release (September 15, 2003) consisted of AbiWord 2.0, Gnumeric 1.2.0, and GNOME-DB 1.0. This was a strategy to give the GNOME desktop environment an office suite of its own, easing the transition for users migrating from platforms where the idea of a dedicated office suite was more or less an expectation.
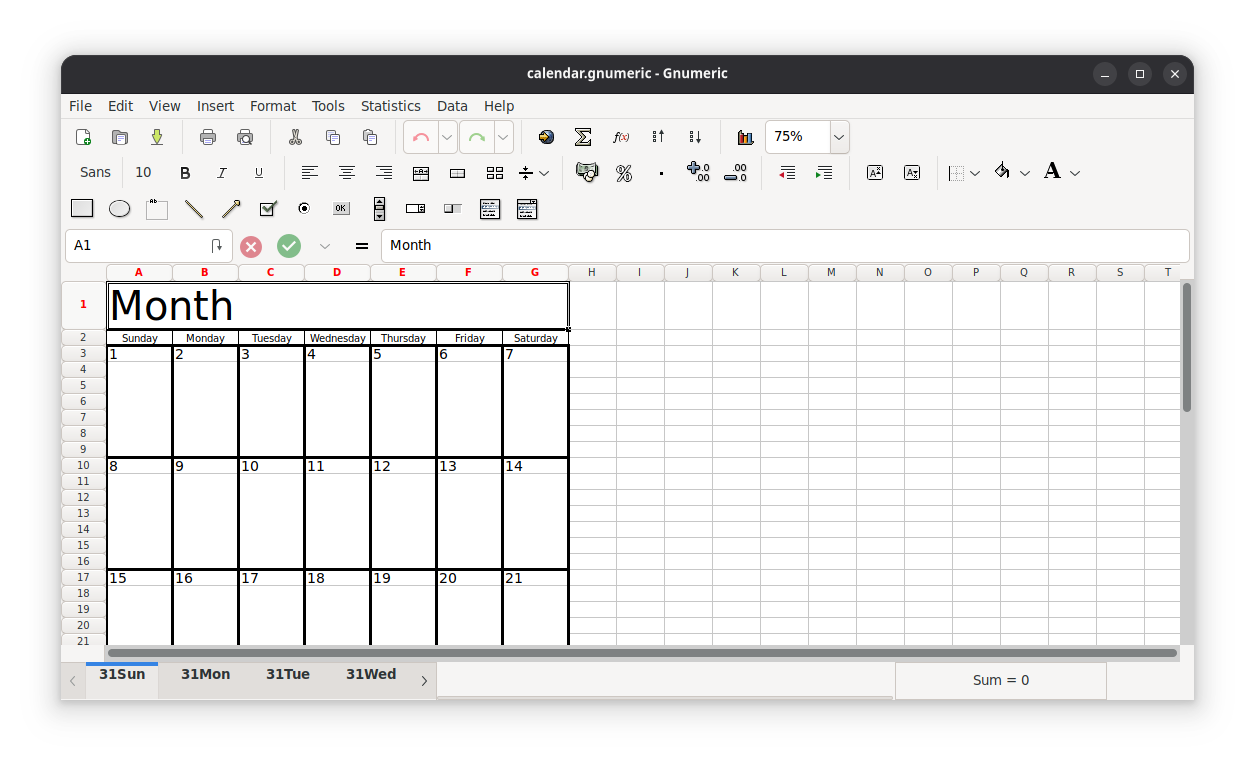
While there was never any subsequent release, in the years that followed, the GNOME Office wiki (now archived) would come to include other applications under this umbrella, including Evolution (for mail and groupware), Evince (for document viewing), Inkscape (for vector graphics), and Ease (for presentations, but now abandoned), to name a few.
All the applications listed there have historically used some version of GTK for their interface and variably used GNOME-associated libraries, such as the now-deprecated Clutter. However, none of them were created for inclusion in any official "GNOME Office suite". Rather, they were adopted under this label once it was recognised that they could serve this purpose.
That said, times have changed dramatically since 2003, and with GNOME increasingly pushing for a place among the larger platforms, now might be a great time for a second look. As it stands, two decades later, GNOME has a mature design system (libadwaita), a clear path for inclusion in the core project, and a solid foundation for a mobile operating system. Yet, except for AbiWord and Gnumeric, which do not fit its current vision, it still lacks robust native applications to fill this niche.
The case for a revival
Platform coherence is one of the strongest drivers of user loyalty, and a powerful argument for a GNOME-native office suite. Not only would it follow the GNOME HIG and use familiar libadwaita widgets, but it would also integrate with portals and GNOME Online Accounts (GOA). A native GNOME Office suite would be mobile-ready, able to scale to phones and tablets on Phosh, thereby delivering the same visual language and behaviours as Files, Settings, and the rest of GNOME Core.
This mirrors how macOS has achieved loyalty through consistent UI/UX patterns, despite lacking the broader market dominance of Windows. As GNOME seeks to secure and protect its vision, an initiative of this kind would encourage distro vendors to bundle more tightly integrated, GNOME-native applications in their default application line-ups.
Furthermore, a dedicated office suite would fill the gaps currently existing in this platform. For example, GNOME has Papers (the replacement for Evince) for viewing documents, and Document Scanner (formerly Simple Scan) for scanning. However, there are no official apps for editing documents.
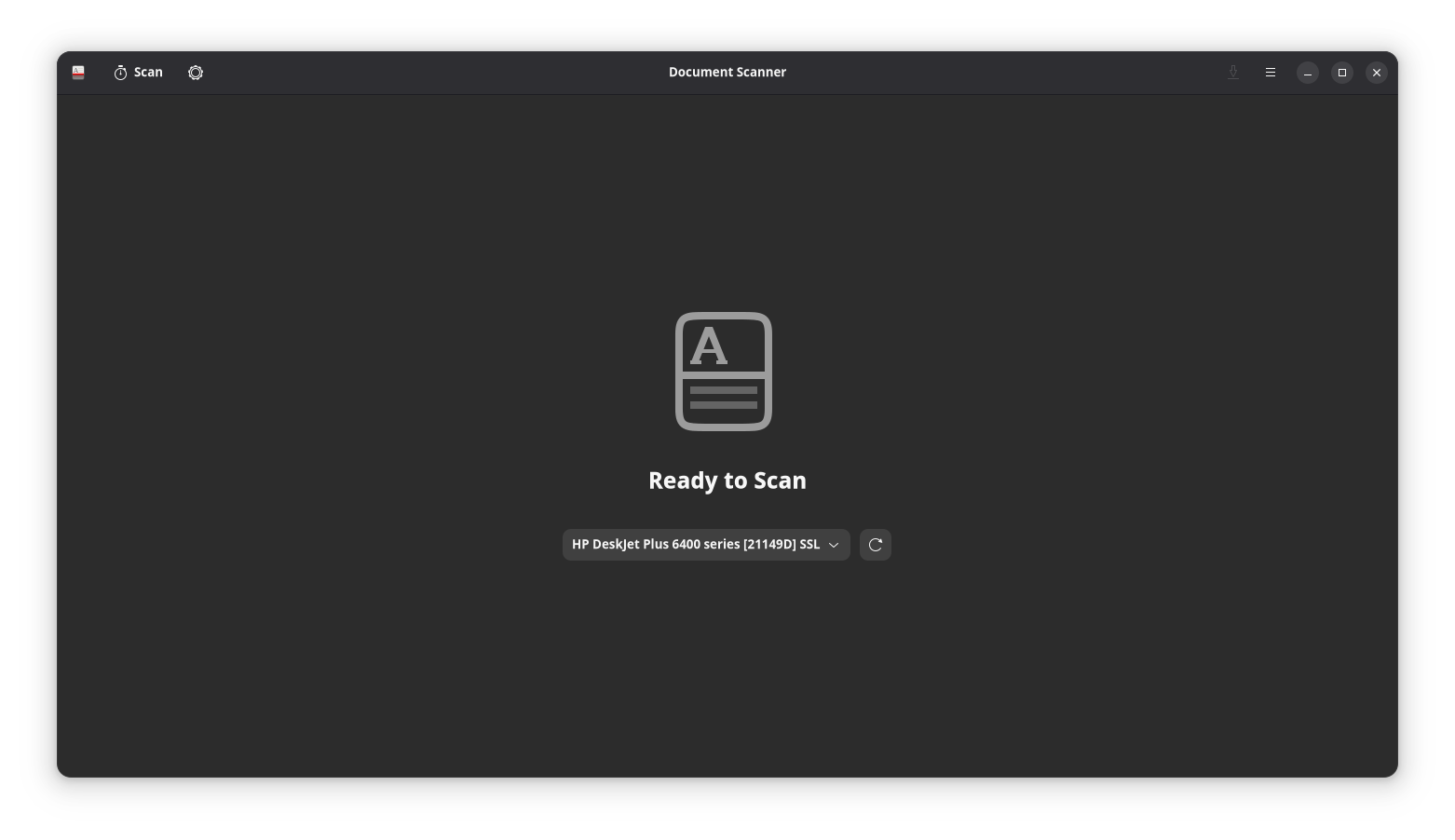
The situation is even worse for other common office formats like spreadsheets and presentations. Without a third-party suite of applications, there are no official GNOME apps for viewing these documents on a standard GNOME desktop. Most distros resolve this by shipping LibreOffice, which works fine, but is notably heavier and does not fit the GNOME aesthetic.
Sure, users could use AbiWord (which is still maintained, believe it or not), or Gnumeric, but neither of these is aligned to the modern GNOME platform. Both Gnumeric and AbiWord use GTK 3, which is under maintenance, not the modern GTK 4/libadwaita stack. This also doesn't solve the problem of a missing presentation solution. LibreOffice works, but it is not designed to be a "GNOME" application. We'll get into the deeper details of why this matters shortly.
All these things considered, there's great benefit to having a lightweight, native suite that not only looks at home, but plays well with its existing office-related apps, including Calendar, Contacts, Loupe (the image viewer) and Document Scanner.
Why now?
In the past, the GNOME project was, for the most part, just a desktop environment - a collection of applications and related libraries that provide a defined and reproducible setup for desktop users. Today, the GNOME project is a lot more than this; it prescribes everything from how applications should look and operate to what system libraries and init systems should be used.
There's even an official reference GNOME distribution, GNOME OS, which brings the project from environment to platform. At this point, having its own office suite is no longer a fancy "nice-to-have" idea. It's almost essential. An official GNOME reference suite would serve as guidance for other applications looking to target the platform.
Aren't existing FOSS office suites good enough?
It's only fair to ask this question, and the answer is a mix of yes and no. Both LibreOffice and ONLYOFFICE provide solid experiences, and the features needed by the average student or professional who may need to do professional work on a modern Linux desktop. Plus, in terms of compatibility with other office suites, like the market-dominant Microsoft Office, both office suites are, for the most part, more than good enough. They are highly compatible with Microsoft's older proprietary formats, and support the ISO open-standard Office Open XML (OOXML)-based formats. LibreOffice even has (limited) support for Excel macros.
However, both suites are designed independently of the GNOME vision, and as such, do not adhere to its HIG, and do not always play well within the desktop environment. Furthermore, while LibreOffice is the most popular of the two, the user experience with its default interface is, to this day, a matter of controversy. To be fair, the same could be said for ONLYOFFICE, as it follows Microsoft's UI design more closely. It really depends on who you ask.
Between the two, LibreOffice is the most widely used across most distros. However, it uses the VCL toolkit for its interface, which has GTK 3/4 backends, but often has notable deficiencies. Work on a GTK 4 plugin for VCL is still ongoing, and the experience using it in GNOME can vary from distro to distro. Furthermore, its interface is admittedly more complex than most GNOME applications and doesn't follow the minimalist guidance that most of them do.
For these reasons, a lightweight, GNOME-focused office suite would actually be better aligned with the project's vision and provide users with a more streamlined experience. It would also allow distributions seeking a purist experience to build upon this vision. For mobile users, it would give them an office suite that's designed for their devices (thanks to libadwaita's strong support for responsive designs). The goal here isn’t to replace LibreOffice or ONLYOFFICE, but rather to complement them with a GNOME-native option that integrates tightly with the platform’s HIG, portals, and mobile ambitions.
What would it take?
There are two possible avenues for this potential revival, should it ever happen:
- Reviving mature code: Upgrading AbiWord and Gnumeric to use modern libraries and changing their interfaces to match.
- Using the Incubator: Creating/adopting new applications to fill these roles within the GNOME project.
Both have their benefits and setbacks, but only one would likely serve the best interests of the project at this time. While converting AbiWord and Gnumeric to GTK4 and libadwaita apps is a possible pathway, the effort involved might be more than it's worth. Not only would both applications need to have their codebases heavily refactored, but their interfaces would need to be changed dramatically. Transitions like these often leave existing users in limbo, and many often don't respond well to removed tools or changed workflows.
This is why the best possible pathway toward a stable GNOME Office platform is to create or adopt new applications into GNOME Core. Under this strategy, a focused trio of applications could enter the GNOME Incubator and, if successful, graduate into the Core with the blessing of the Release Team. Already, there is at least one application that could be a candidate for a future GNOME Office's word processor/document editor: Letters. Written in Python, this application was recently released to Flathub, supports the Open Document Text (ODT) format, and follows GNOME's minimalist design.
Like Calligra Words, the word processor from KDE's office suite, it does not support the full gamut of features available with ODT, but for the purpose of providing basic functionality, it's at least sufficient. Also, to be fair, the app is rather new, having been released in October of this year (2025). From a technical standpoint, it uses the Pandoc library, which means it can support a vast array of text documents without any extra dependencies.
At this time, there seem not to be any equivalent applications for presentations or spreadsheets, but in theory, these applications could be swiftly built on existing libraries. For instance, a presentation editor could be built on GTK4 and libadwaita using odfpy and python-pptx for providing file format support. A spreadsheet editor could be created on top of the same UI libraries and use liborcus and ixion for providing file format support and the underlying logic.
Alternatively, GNOME Office already has useful libraries for building office applications: libgsf handles structured document I/O (ZIP/OLE2, streams, metadata), while GOffice provides charting and spreadsheet-oriented utilities (the same stack Gnumeric builds on). Together, they could prove a solid core beneath a GTK4/libadwaita interface.
If these (theoretical) apps were to be written in a popular and accessible language like Python, as with Letters, it's even more likely that the community would be able to take over if, at any time, development were to slow down. Neither app would need to support the full features of their relevant formats. All that the average user needs is to be able to produce simple presentations and spreadsheets with what they have on their system. For those who need full functionality, there's always the option to install and use a fully-featured suite like LibreOffice or ONLYOFFICE.
Conclusion
Now that GNOME has everything in place to serve as a full platform, it's well-positioned to have first-party answers for documents, spreadsheets, and presentations that fit the GNOME way. A small, native GNOME Office would not replace LibreOffice or ONLYOFFICE. It would sit beside them and cover the basics with a clean, touch-friendly, libadwaita interface that works on laptops, tablets, and phones. The building blocks already exist. At this point, all that is missing is a focused push to turn them into real apps and bring them through the Incubator.
/// 5 Nov 2025, 4:40 pm ////// Blackmoreops ///
Step by step guide on how to add free enterprise-grade Two-Factor Authentication in WordPress using Cisco DUO. A complete guide with screenshots for bulletproof security in under 15 minutes.
The post How to Add Two-Factor Authentication in WordPress for Free appeared first on blackMORE Ops.
/// 5 Nov 2025, 5:30 am ////// Tecmint ///
Debian offers several tools for managing software packages, each serving a specific purpose in the package management ecosystem, and understanding
The post How to Use dpkg, apt, aptitude, synaptic, and tasksel in Debian first appeared on Tecmint: Linux Howtos, Tutorials & Guides./// 4 Nov 2025, 8:00 am ////// Fedora Magazine ///

The official dates and location are set for Flock to Fedora 2026, the premier annual conference for Fedora Project contributors. The event will take place from 14-16 June 2026, in Prague, Czechia.
For Flock 2026, we are returning to the Vienna House by Wyndham Andel’s Prague, located at:
Stroupeznickeho 21
Prague, 150 00
Czech Republic
While all three days will be full conference days, the arrangement of the schedule will change slightly in 2026. Sunday, 14 June, will be designated as Day 0, featuring workshops, team meetups, and hands-on contributor sessions. The main conference activities, including streamed content, the opening keynote, and other sessions, are scheduled for Monday, 15 June, and Tuesday, 16 June.
Coordinated Scheduling with DevConf CZ
Following community feedback from last year, Flock 2026 has been scheduled to align more closely with DevConf.CZ. The conference will conclude just before DevConf.CZ begins in Brno (18-20 June 2026). This compressed travel schedule is intended to make it easier for community members who wish to attend both events.
Call for Proposals & Conference Themes
The Call for Proposals (CFP) for Flock 2026 will open in early December 2025 and close shortly after FOSDEM 2026 (31 January – 1 February). Speaker confirmations are scheduled to be sent in March 2026.
For Flock 2026, we are taking a more focused approach to session content. The Fedora Council, FESCo, and the Mindshare Committee are shaping key themes for the CFP. All presentation and workshop submissions should align with one of these themes. More details will be shared when the CFP opens.
Planning for Flock 2026
Here is what you need to know to plan your attendance:
- Registration: Conference registration is scheduled to open in January 2026.
- Sponsorship: Is your company or organization interested in sponsoring Flock 2026? Our sponsorship prospectus for Flock 2026 is now available on the Flock 2026 website. Organizations interested in supporting Flock and the Fedora community are encouraged to review the prospectus and contact the organizing team with any questions.
- Hotel Block: A discounted block of rooms is arranged at the conference hotel. More information about the discounted hotel block can be found on the Flock website.
- Travel Day & Connections: 17 June is designated as a free travel day between Flock to Fedora 2026 and DevConf.CZ. Frequent bus and train connections are available for travel between Prague and Brno.
- Sponsored Travel: We intend to offer sponsored travel again for Flock to Fedora 2026. More details will follow in December 2025.
Get Involved & Ask Questions
The official Flock to Fedora 2026 Matrix room, #flock:fedoraproject.org, is the best place to connect with organizers and other community members. We encourage you to join the channel for the latest updates and to ask any questions you may have.
A Note on Our Flock to Fedora 2026 & 2027 Plans
We recognize that returning to the same city and venue for a second consecutive year is a departure from Flock’s tradition. This decision was made intentionally with two key goals in mind.
First, by working with a familiar venue, our organizing team can optimize its processes and plan further in advance. This stability for Flock to Fedora 2026 will give us more opportunity to improve our internal processes and explore new ways to incorporate community input into the design of Fedora’s flagship contributor conference.
Second, this allows us to plan for a significant change in 2027. The Flock organizing team is committed to exploring new locations for Flock 2027, with a particular focus on regions outside of North America and Europe. We acknowledge the travel difficulties many of our contributors in regions like LATAM and APAC face. We learned valuable lessons from past planning cycles and are eager to achieve this goal, while also recognizing that unforeseen circumstances can impact our plans. We will work with community members in these regions to explore possible options and conduct thorough research on pricing and availability for 2027.
We look forward to seeing you in Prague for Flock 2026, 14-16 June.
— The Flock to Fedora Planning Team
/// 5 Nov 2025, 3:33 pm ////// The Hacker News ///
/// 5 Nov 2025, 4:26 pm ////// 9to5Linux ///

Fwupd 2.0.17 Linux firmware updater is now available for download with support for ASUS CX9406 touch controller, Framework Copilot keyboard, and other devices.
The post Fwupd 2.0.17 Released with Support for Lexar and Maxio NVMe SSDs appeared first on 9to5Linux - do not reproduce this article without permission. This RSS feed is intended for readers, not scrapers.